Best Cyber Security Certificate Course in Bhubaneswar
Get ready for Top-tier Cyber Security Certification Program

Our Cyber Security Certification Course In Bhubaneswar equips learners with the practical skills and knowledge required to defend digital systems in today’s cyber-threat landscape. Focused on real-world scenarios, the program covers ethical hacking, network security, penetration testing, and incident response—all designed to prepare you for top roles in the cyber security domain. With hands-on training, expert guidance, and a career-focused curriculum, you’ll gain the tools needed to detect vulnerabilities and safeguard critical data. Enroll in our Cyber Security Training Institute in Bhubaneswar and start your journey toward a high-demand career as a Cyber Security Analyst, Ethical Hacker, or SOC Specialist in the ever-evolving world of digital defense.
Who Should Take our Cyber Security Course?
Our Cyber Security Course In Bhubaneswar is perfect for anyone aspiring to build a rewarding career in Cyber Security, Ethical Hacking, or Information Security. Whether you’re a student, a working professional looking to transition into the cyber security field, or a tech enthusiast aiming to develop expertise in network protection, penetration testing, and cyber threat mitigation, this course is for you. Designed for both beginners and experienced professionals, our program delivers industry-relevant skills and hands-on training that prepare you for real-world challenges. If you aim to become a Cyber Security Analyst, Ethical Hacker, or SOC Specialist, or simply want to upskill in one of today’s most in-demand fields, our Cyber Security Certification in Bhubaneswar provides the knowledge and tools to help you achieve your career goals.
The Importance of Cyber Security in Today’s Tech-Driven World
In today’s hyper-connected and digital-first world, Cyber Security has become a mission-critical skill for individuals and organizations alike. With the rise in cyber threats, data breaches, and ransomware attacks, the demand for professionals skilled in network security, ethical hacking, and digital forensics is at an all-time high. Learning Cyber Security not only protects digital assets but also opens doors to high-paying, future-proof careers. Whether you’re managing business infrastructure or simply looking to secure your personal data, mastering Cyber Security skills is no longer optional—it’s essential. Enrolling in a Cyber Security Course in Bhubaneswar is the first step toward becoming a sought-after expert in safeguarding the digital world.

Cyber Security Course Overview
Our Cyber Security Course In Bhubaneswar is designed to equip learners with a strong foundation and advanced knowledge in cyber defense, ethical hacking, and information security. This comprehensive program covers critical topics such as network security, penetration testing, vulnerability assessment, cryptography, and incident response, preparing you to protect systems and data in real-world environments. From identifying potential threats to implementing robust security measures, this course empowers you to combat cyber risks in today’s digitally connected world.
Focused on practical learning, the course includes real-time labs, hands-on simulations, and industry-based case studies, giving you the experience needed to handle real-world cyber security challenges. Whether you’re a beginner aiming to enter the cybersecurity field or a professional looking to advance your career, this program provides the skills and confidence to succeed in high-demand roles like Cyber Security Analyst, Ethical Hacker, and SOC Specialist.
Tools Covered
Our Cyber Security Course In Bhubaneswar covers essential tools like Kali Linux, Wireshark, Nmap, and Burp Suite for ethical hacking, network analysis, and vulnerability assessment. You’ll also gain expertise in advanced tools such as Metasploit Framework for exploitation, Snort for intrusion detection, and OWASP ZAP for web application security testing. Additionally, tools like Cisco Packet Tracer and Nessus are included for network simulation and vulnerability scanning. These industry-relevant tools ensure you’re well-equipped to tackle real-world cyber threats and build a successful career as a Cyber Security Analyst, Ethical Hacker, or Information Security Expert.

Why MoxieTEK is the Best Choice for Cyber Security Course in Bhubaneswar
-
Comprehensive Curriculum: Industry-aligned training covering Cyber Security fundamentals, Ethical Hacking, Network Security, Penetration Testing, and Incident Response.
-
Hands-On Learning: Real-world labs, simulations, and case studies to build practical skills in tackling cyber threats.
-
Expert Trainers: Learn from seasoned professionals from top MNCs with extensive experience in Cyber Security and Information Security.
-
100% Placement Assistance: End-to-end career support to help you land top roles in leading tech and security firms.
-
Pay After Placement: Pay 40% of the course fee only after securing a job, making your investment safe and risk-free.
-
NASSCOM Certification: Gain a prestigious NASSCOM-accredited Cyber Security Certification, validating your expertise and boosting your resume.
-
Affordable Fees: High-quality, career-focused training at student-friendly pricing.
-
Flexible Learning Options: Choose between online and offline classes that fit your schedule.
-
Local Expertise: Recognized as one of the best Cyber Security training institutes in Bhubaneswar, trusted by students and professionals across Odisha.
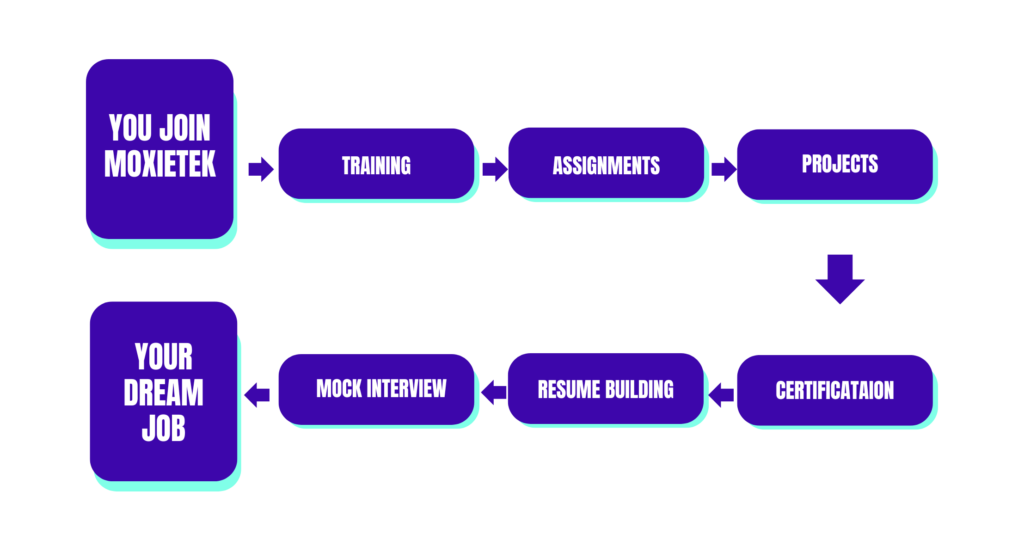
How MoxieTEK Guides You From Enrollment to Your Dream Job
Cyber Security - Avg. Annual Salary
No Data Found
No Data Found
Cyber Security Curriculum
- Introduction
- Hardware and Basics of Networking
- Installation of Server
- Active Directory
- Member Server/Client and User Management
- Permissions
- Profiles
- Roles of Active Directory
- Group Policies
- DHCP
- DNS
- Web Server
- FTP Server
- Routing (Static/Dynamic)
- Remote Access Service (RAS)
- Disk Management
- Routers-Port and Vulnerability Scanning
- Firewalls
- Network Attacks, Architecture, and Isolation
- Wireless and Wi-Fi Security
- Network Monitoring for Threats
- Search Engines and Privacy
- Browser Security and Tracking Prevention
- Passwords and Authentication Methods
- Introduction
- Kali Installation
- Terminal Basics: Commands I, II, III, IV, V, VI, VII, VIII, IX, X and XI
- Permissions I and II
- Anonymity
- Proxy
- VPN I and II
- TOR I, II and III
- Proxychains
- Change IP/MAC
- DNS Enumeration
- NMAP I/II/III
- Search Exploit
- Website Footprinting
- Vulnerability Analysis
- Live Attack
- Security Audit
- Password Attack
- Password Cracking
- Wireshark
- Spoofing (Ettercap I/II)
- Fern
- Metasploit
- Buffer Overflow
- BeEF
- Introduction to ethical Hacking
- Foot printing and Reconnaissance
- Scanning Networks
- Enumeration
- Vulnerability Analysis
- System Hacking
- Malware Threats
- Sniffing
- Social Engineering
- Denial-of-Services
- Session Hijacking
- Evading IDS, Firewalls and Honeypots
- Hacking Web Servers
- Hacking Web Applications
- SQL Injections
- Hacking Mobile Platforms
- IoT and OT Hacking
- Cloud Computing
- Cryptography
- API Security Risks
- OWASP Top 10 API Security Risks – 2023
- API1:2023 Broken Object Level Authorization
- API2:2023 Broken Authentication
- API3:2023 Broken Object Property Level Authorization
- API4:2023 Unrestricted Resource Consumption
- API5:2023 Broken Function Level Authorization
- API6:2023 Unrestricted Access to Sensitive Business Flows
- API7:2023 Server Side Request Forgery
- API8:2023 Security Misconfiguration
- API9:2023 Improper Inventory Management
- API10:2023 Unsafe Consumption of APIs
- Introduction
- Emerging Threat Landscape
- Implementing Cyber Risk Management
- Classifying Information and Data, DLP
- Compliance and Governance
- Security, Privacy, Regulatory & Compliance Controls
- Access Controls, IAM & PAM
- Using the MITRE ATT&CK Framework
- Defining a Security Operations Center
- People, Personnel Development, Retention and Attracting Talent for a SOC
- PROCESS
- PROCEDURES
- Dashboards & Use Cases
- Automation
- Continuous Training
- Secure Code Review & Application Security
- Security Monitoring
- Introduction To Threat-Hunting
- Threat-Hunting Step-by-Step
- Threat Intelligence: The Intelligence Life-cycle
- Threat Intelligence: Step-by-Step
- Common Security & SOC Use-Cases
- Open-Source Intelligence (OSINT)
- Splunk & Elastic Search as SOC Dashboards
- Tabletop Exercises
- Offensive Security.
- Cloud Computing Security
- Firewalls, IDS, IPS, UTM & Firewall Rule Management
Address
Phone: +91 70777 04010

